Introduction to Incident Management
Quick introduction to the module key capabilities
The Incident Management module helps you to systematically manage your Security Incidents. The module allows you to define the Incident Lifecycle by using user-defined stages that every Incident must go through before is closed.
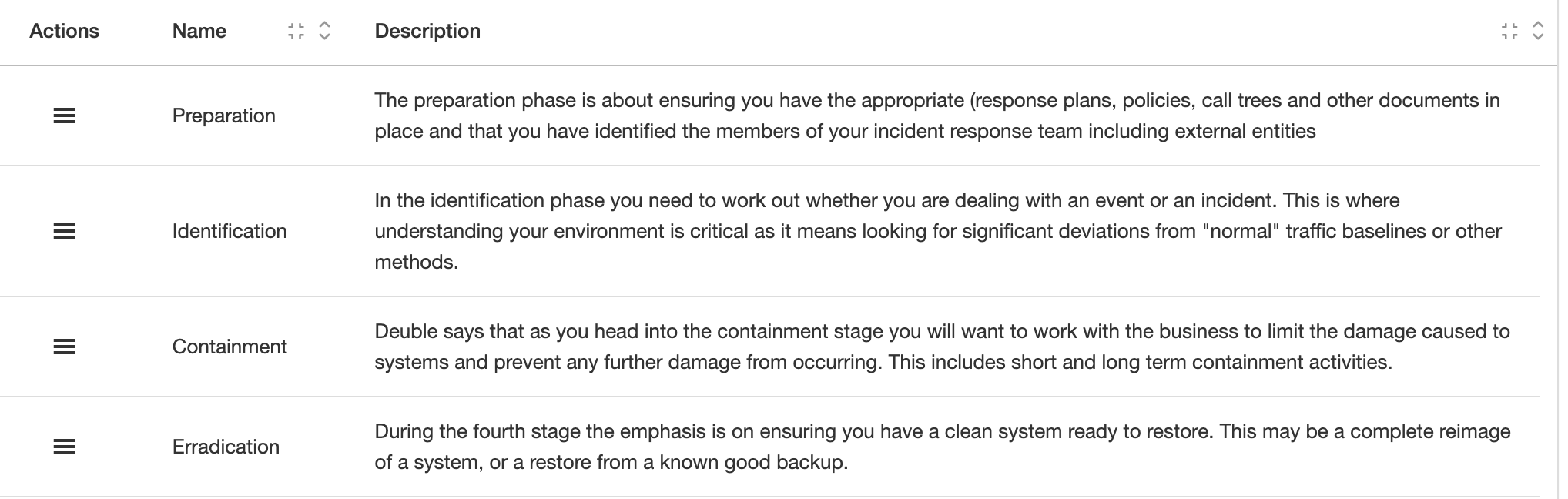
Stages are used to ensure all incidents are treated systematically and also to document findings and related events that pop up during the incident lifecycle.
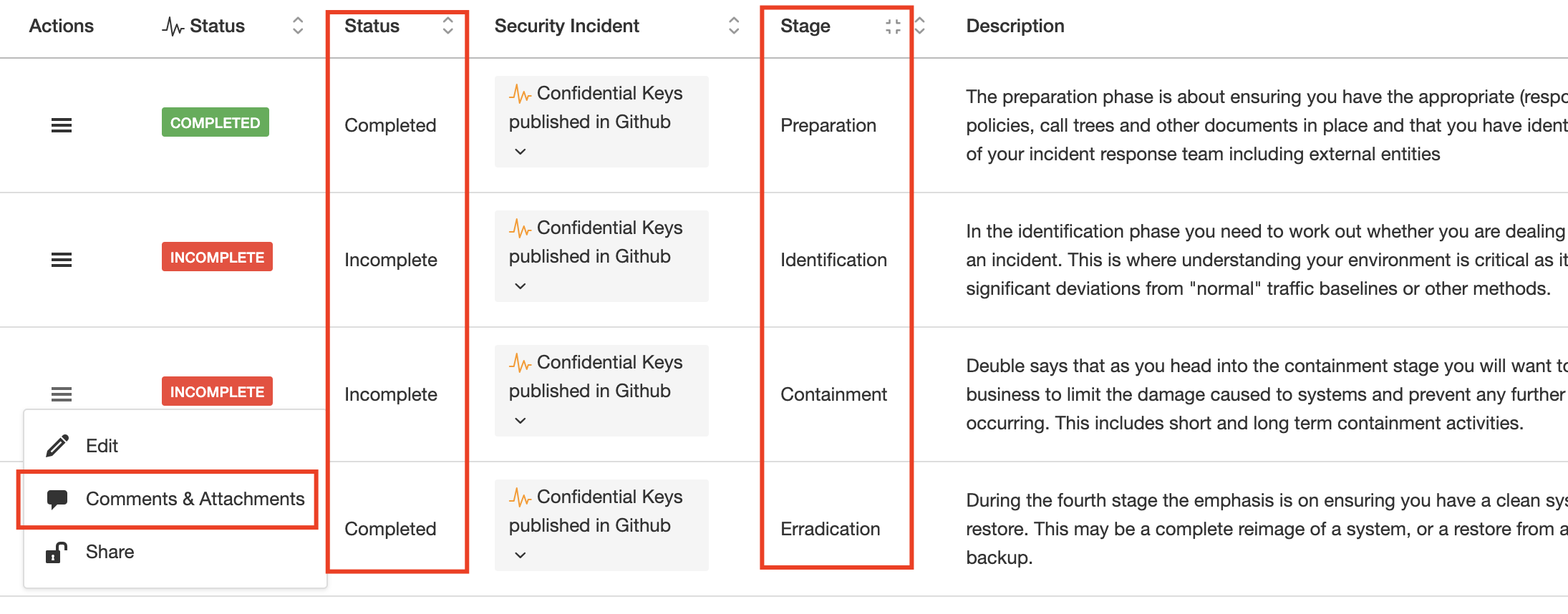
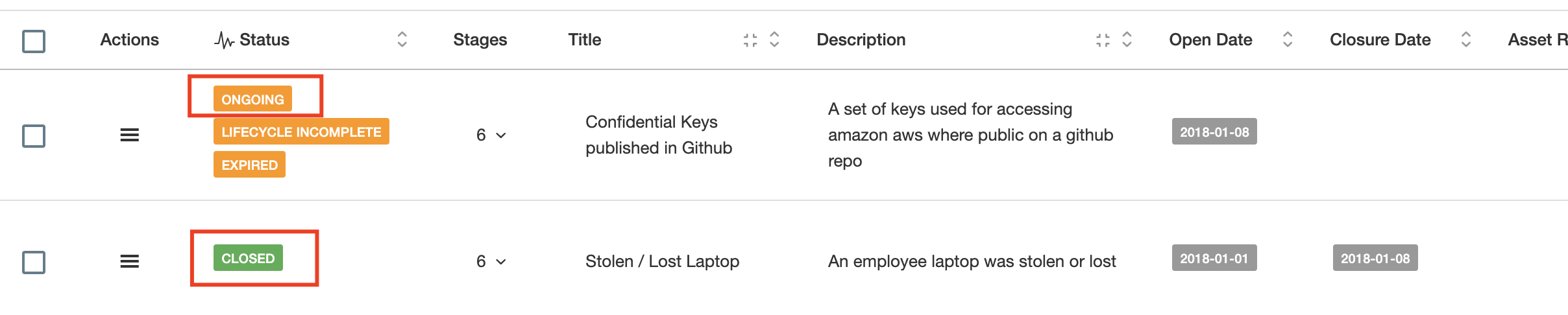
The use of Statuses allows you to quickly identify the situation of every incident and in particular if the lifecycle has been completed or not.
Incidents are derived from two typical scenarios:
- Problems (Risks in eramba) that we knew could happen and for which we have some treatment and containment plan (this information is stored in the Risk module)
- Problems we did not know or did not consider properly.
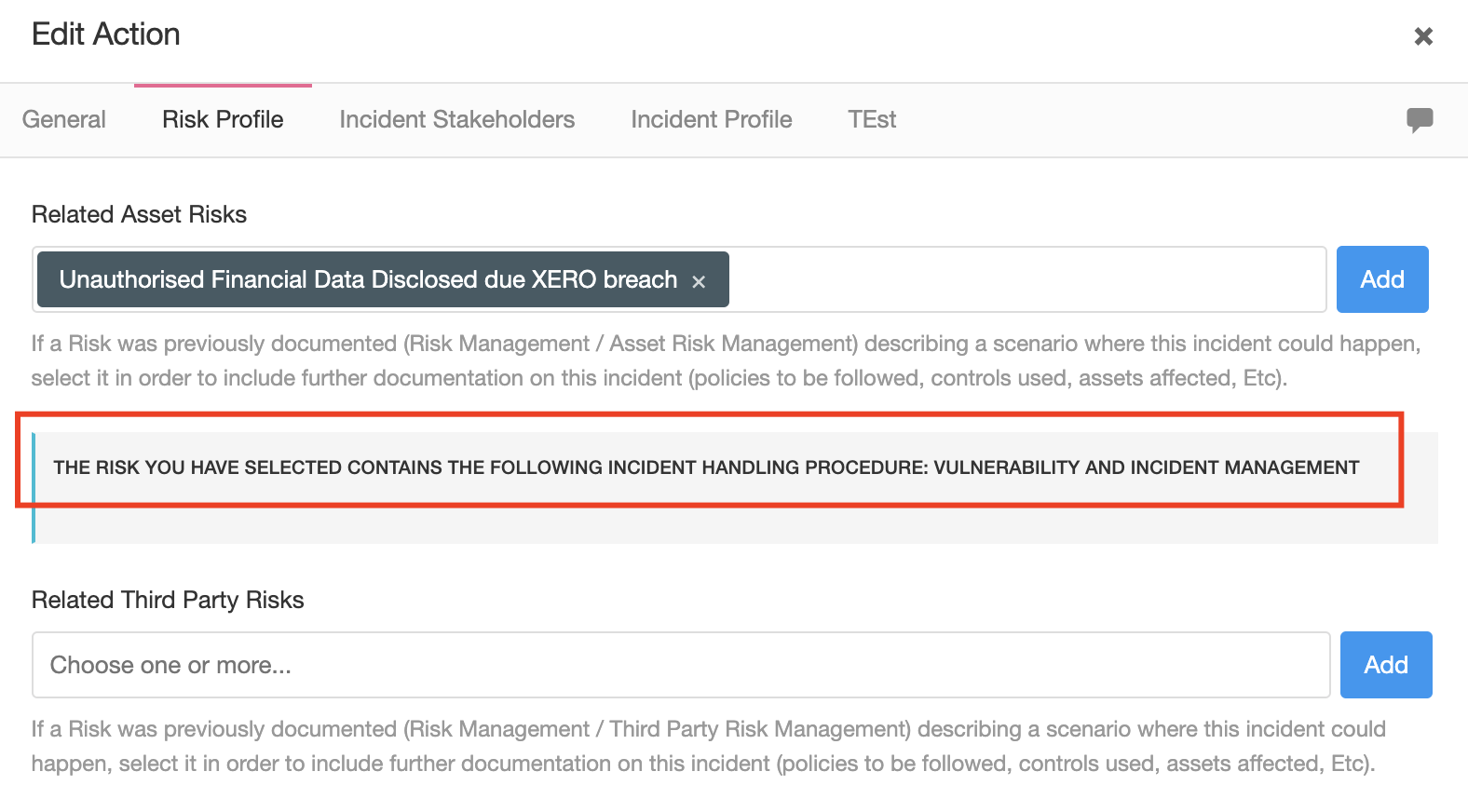
For this reason, when you create incidents in eramba you can tie them to existing Risks (Asset, Third Party or Business) from the Risk module.
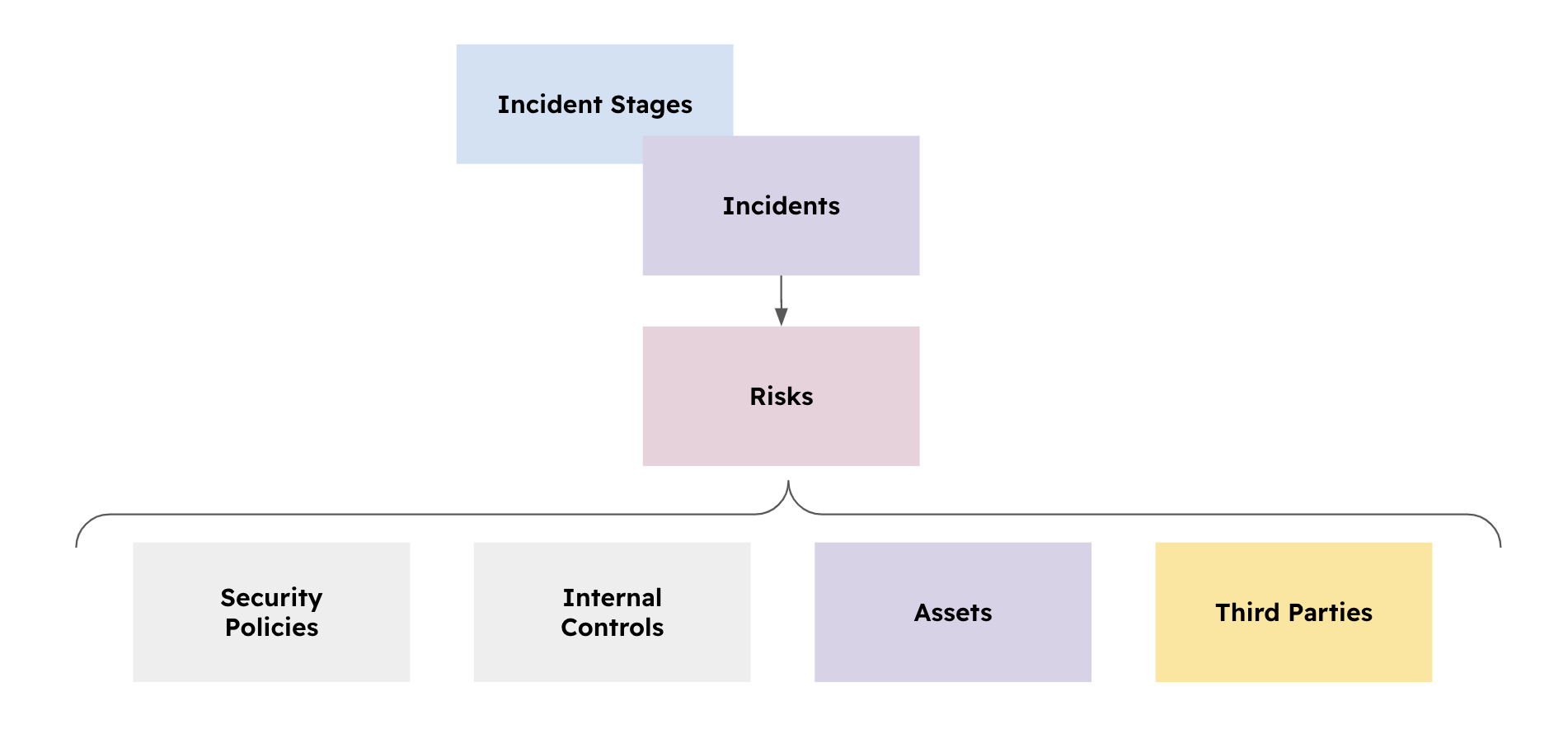
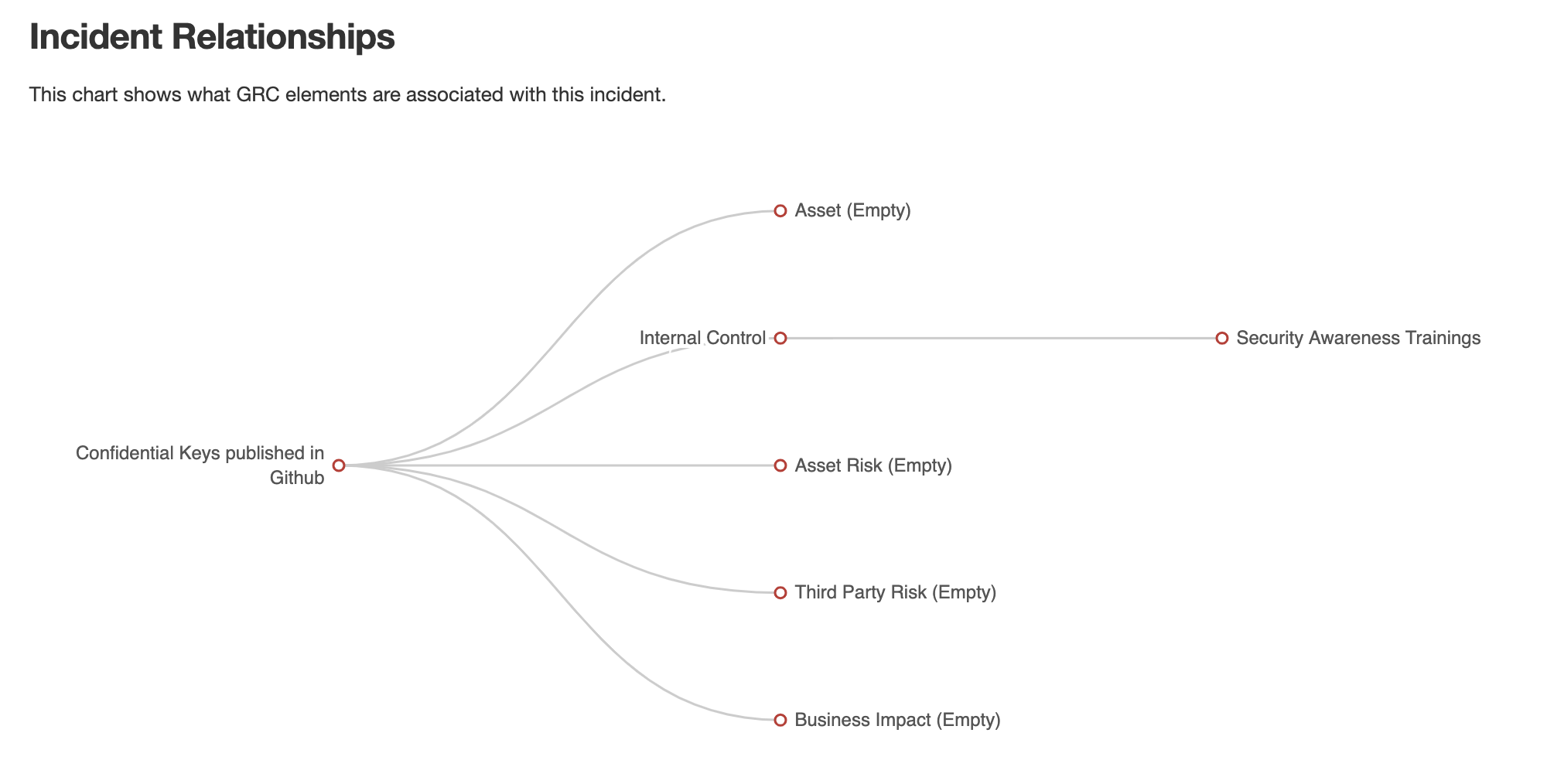
When such an association happens (at the time of creating the incident) eramba will populate the Incident with the Risk contextual information, this should provide the incident handler with some background as to elements that could be affected:
- Policies
- Internal Controls
- Assets
- Third Parties
If you defined containment procedures for your Risks they will also be shown to your incident handles, this will be useful to know how to respond to a known problem.
As with any other module in eramba you can use Reports to describe Incidents in a more graphical way and use Filters, Notifications and Statuses to manage their lifecycle.
The incident module handles receiving REST API calls that allow all common CRUD actions. This is often times used to automatically create incidents when systems around identify them. You can also trigger API calls from eramba to other systems using user-defined status.
Playlist
- Episode 1Start Here1 min left
- Episode 2Introduction to Risk Management - old13 mins left
- Episode 3Introduction to Compliance Management - old16 mins left
- Episode 4Introduction to Data Privacy1 min left
- Episode 5Introduction to Incident Management7 mins left
- Episode 6Introduction to Online Assessments11 mins left
- Episode 7Introduction to Awareness Programs1 min left